How does the Rejust.ro platform work?
With 3 clicks, and using the phrase "use the password," the case files could be accessed through ReJust.ro
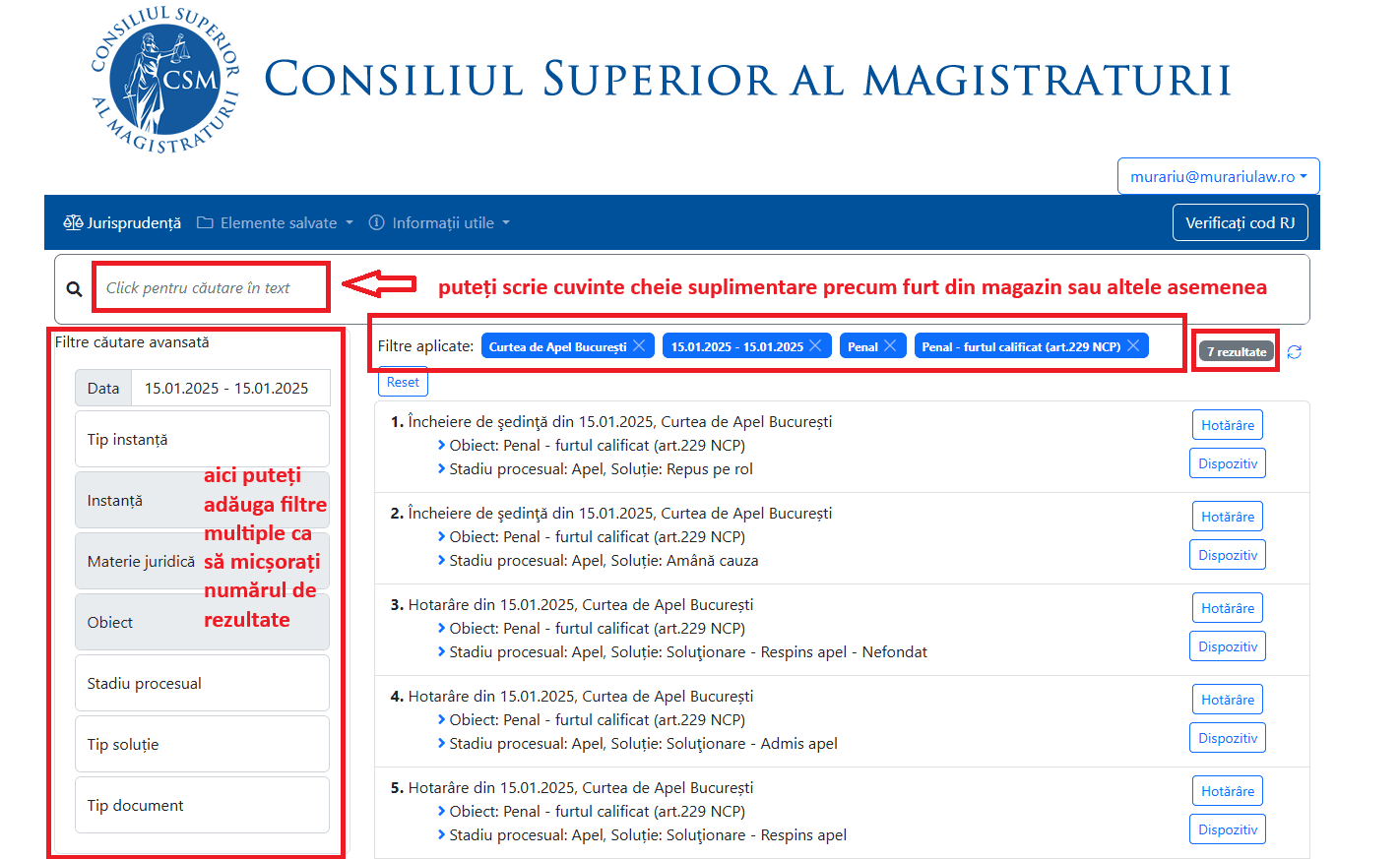
The ReJust.ro platform is the application through which legal professionals and ordinary citizens can consult anonymized versions of court cases.
In normal circumstances, this application must not include personal information that could jeopardize the parties involved in the case, and on the other hand, it should provide legal professionals with access to the information they need to understand the courts' behavior regarding certain common or recurring cases.
The platform must therefore balance the need for information for the parties involved with the need to securely protect the sensitive data of the parties, witnesses, etc.
Update 27.08.2025: Information about the VIDEO breach
What was, in fact, the gap of ReJust.ro?
The main issue affecting ReJust.ro was due to the lack of accountability among the judges in the courts, combined with the absence of measures taken by the platform's managers - namely, the Supreme Council of Magistracy.

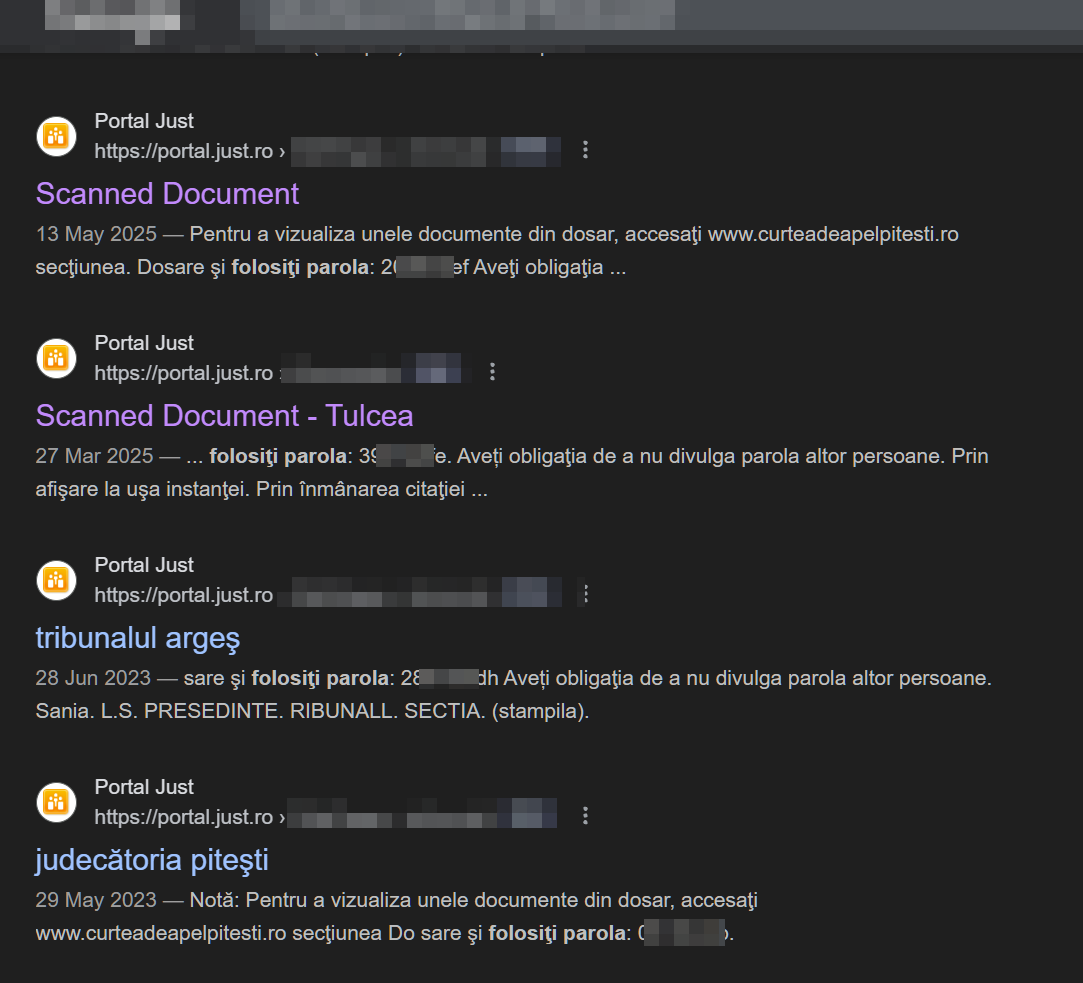
Firstly, many files were completely non-anonymized, using blue ink to "anonymize" the access password to the file.
The number of files susceptible to this form of negligence is in the hundreds, but it demonstrates firsthand the lack of attention given to how the data is subsequently processed or even published.
The professional negligence of the clerks, combined with the institutional indifference of the CSM, has led to the unresolved issue of a severe vulnerability, lacking technical character. Specifically, anyone could search on rejust for the phrase "use the password" to obtain a list of over 170,000 vulnerable cases.
The method by which the vulnerability was exploited. You would enter the site, log in, search for "use password," and obtain a list of all files that had a public password. Then, you would click on the decision, click on download, and scroll down where the password was no longer censored in the downloaded document. That was the vulnerability, and anyone could do it with zero IT knowledge.
It is evident that the term without a user (in this case, the case number is unnecessary), but this aspect can be easily rectified if we consider that: a) the number of cases in a specific court, with a specific subject, on a specific date is under 10, even in the busiest courts. b) The dosare.just.ro system allows advanced searches using an API, and most case search tools now also permit advanced searches.
Practically, you should retrieve the case details from rejust.ro and search for 2-3 cases on just.ro. Verify and compare the device that helps you accurately identify the specific case at hand.
Thus, you also had the case number that you could retrieve from rejust.ro. Similarly, the search can be conducted on rejust.ro using the data from just.ro.
With both, you had access to the electronic file, which you would connect to.
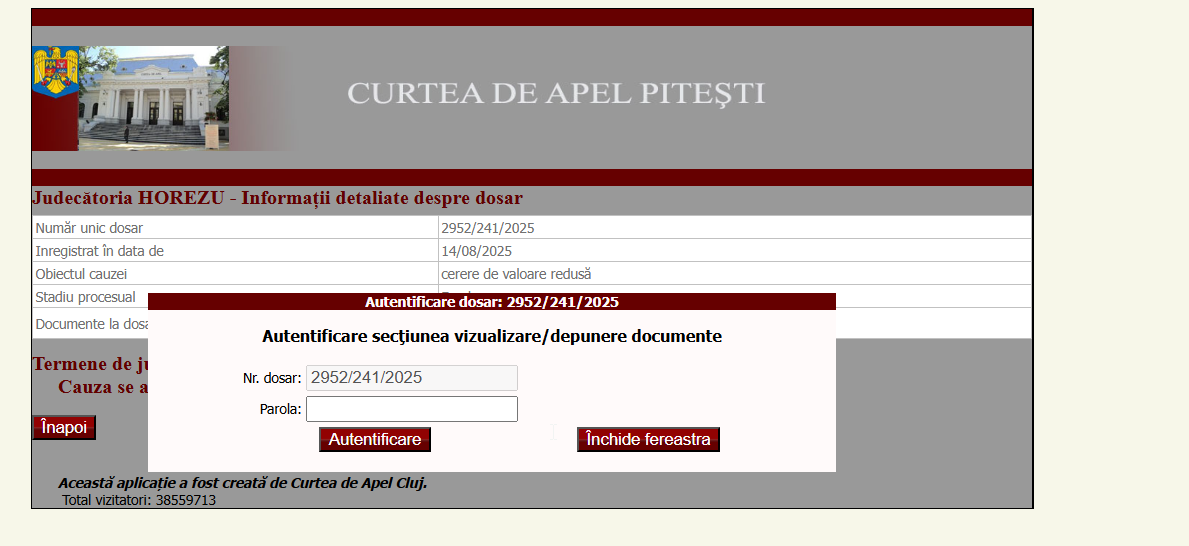
The next step for a malicious actor would have been to use this knowledge to exfiltrate sensitive data and initiate blackmail or information-gathering campaigns, etc. Hence, the severity of the situation.
Once the file on rejust.ro is de-anonymized and the password is obtained, you will have full access to the electronic file with both the username and password.
How did we discover bresa?
The first breach in the notification sent to CSM in August 2024 was this one, and I learned about it from a friend who is a tax consultant. The issue was so simple that he discovered it and incidentally mentioned it to me, but he did not report it. I reported it to CSM myself.
The second breach will provide more details as I ensure that it has been resolved and the risk is minimal to nonexistent for victims to be affected by any potential premature disclosure, even if it were due to the fault of the CSM.
Who does this breach affect?
Approximately 170,000 cases are in the jurisdictions of Constanta, Cluj, Targu Mures, Pitesti, Craiova, Timisoara, any court that used the electronic case management platform of the Cluj Court of Appeal.
The majority were concentrated in Constanta, Cluj, and Pitesti. Some of the results indicate other passwords, but these account for approximately 10% of the files. Out of all the files reviewed to validate the existence of the breach (~20-30), only 2 were false positives, meaning only 2 were counted additionally.
We estimate that the actual number of vulnerable files was around 150,000, plus those affected by another breach that will be detailed later, and this represents a lower level of difficulty compared to the current breach.
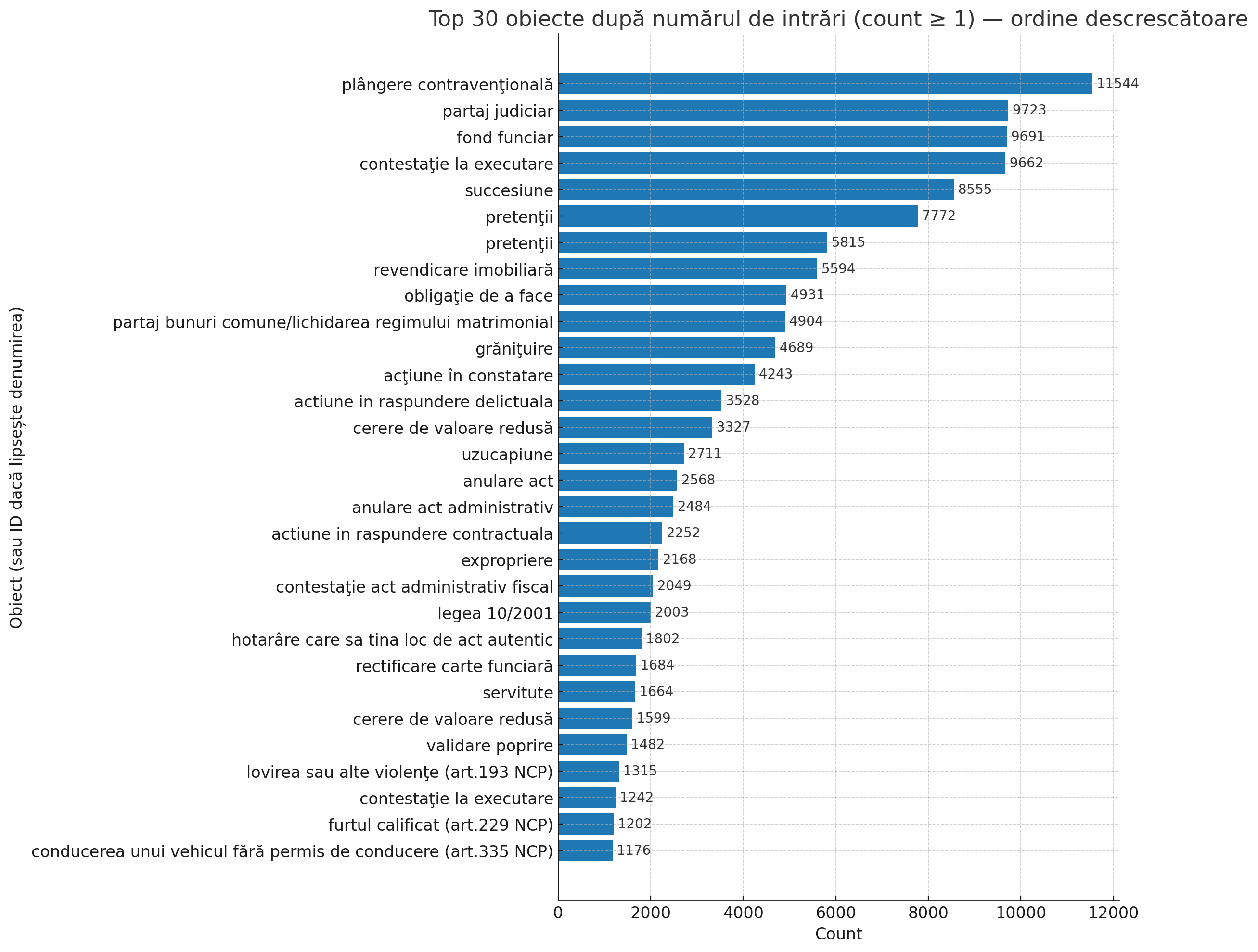
The category with the highest risk of systematic exploitation consists of family and minor-related cases. These include 4,904 cases of asset division and matrimonial regime liquidation, 837 cases of parental authority exercise, 688 cases of maintenance pension, and 129 protection orders.
This documentation contains sensitive personal data, including addresses, financial information, and psychological assessments, representing priority targets for intelligence gathering and social engineering operations.
In the field of economic crime, the 376 tax evasion cases and 698 insolvency requests represent valuable resources for organized economic crime groups. Information about financial schemes, bank accounts, and business relationships can be monetized through extortion, insider trading, or sale on underground markets.
Sensitive criminal records, including 136 cases of domestic violence, 52 cases of pimping, and 20 cases of human trafficking, present a high risk of re-victimization. Organized crime groups may use this data to identify vulnerable victims or to protect their operations by compromising witnesses.
Property disputes, represented by 9,662 enforcement challenges and 8,555 inheritance cases, provide valuable intelligence for targeted attacks. APT actors can leverage this information for spear phishing, pretexting, or other techniques aimed at compromising individuals with significant assets.
What actions have the public authorities taken?
The DNSC has done its job and notified the responsible authorities.
No one has been sanctioned for the situation created, no measures have been taken against anyone for the issue, and they do not seem to have trained the clerks to prevent this situation from happening in the future.

The CSM Secretary responded curtly, stating in principle that the terms and conditions provide sufficient protections to safeguard litigants from any potential inquiries.


The Court of Appeal Constanta has requested that we communicate the vulnerable aspects to the authorities, stating once again that anonymization by name is sufficient to protect the case number.


The judicial inspection argued that there is neither any problematic act nor any form of gross negligence that led to the publication of passwords in summonses, which are public documents.
ANSPDCP has communicated to us that it is not the authority responsible for overseeing and sanctioning any potential data breaches by the judiciary, as this role belongs to the CSM. The CSM has not self-sanctioned, preferring to conceal the issue and not apply the GDPR regulations.

After nearly 12 months, I revisited the previously reported vulnerable websites to check if the issue had been resolved. I found that the resolution was superficial, still allowing access to files through the password.
This morning, I re-notified the institutions and initiated the disclosure procedure regarding the existence of the vulnerability in a manner that does not pose a risk to the victims. Due to public pressure, the CSM resolved the issue in record time.

At 11:04 am, I confirmed the resolution of the issue by checking the platform multiple times to ensure there are no risks of sensitive data disclosure.

I have confirmed the issues reported to the judiciary as resolved in the previous days. Regarding those mentioned by the court, the following criticisms arise:
- Even if the site indirectly accesses the ecris system, there is a risk that once inside the system, a malicious actor could achieve privilege escalation, especially given the outdated tech stack and the neglect of cybersecurity standards in the application development. Therefore, the mere existence of the current breach indicates that the underlying problems are likely much more severe, and any motivated malicious actor risks identifying and exploiting them.
- We hope that their analysis is thorough.
- Very well.
- The problem was that SQL injection could be performed (interacting directly with the database accessible to the web application) through the application's ID, rather than the issue being that you could access other files.
- Very well.
Response from the authorities post re-notification (Updated 14:43 18.08.2025):
I propose below to make the interaction with the Romanian state as transparent as possible, in order to compel the constructive resolution of issues and the implementation of measures to reduce the risk of similar problems persisting.
Thus, I ensure that the authorities cannot deny their awareness of the issue or attempt to seek solutions outside the legal framework.
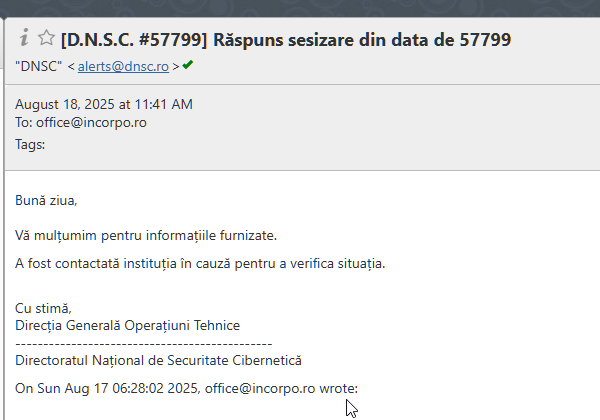
Formal interactions (contact):

Interactions with the web platform:
Using web log analysis techniques, I examined the access areas of the application to highlight the interaction of public authorities with the breach.
Interactions - National Cyber Security Directorate
The first interaction from the DNSC took place at 9:00 AM on August 17, 2025, prior to the resolution of the vulnerability by the CSM, likely as a result of the DNSC's intervention.
He strictly targeted the main page of the site, probably to identify the source of the notification sent a few hours earlier to the institution.
Interactions - Romanian Intelligence Service
A short duration of average sessions indicates more of an informational scanning activity, where operators quickly reviewed the content to identify the themes and level of public exposure, without delving into a detailed analysis of each material.
This type of behavior is characteristic of preliminary checks or awareness reports, intended to provide decision-makers with a concise overview of reputational risk and potential institutional implications.
Interactions - National Anti-Corruption Directorate
We have monitored long-duration interactions from an IP associated with the National Anti-Corruption Directorate, which demonstrate the involvement of anti-corruption authorities in the breach analysis. Access began at 10:00 AM during working hours.
Extended duration of web sessions (where the browser tab was intermittently opened), with successive navigation through the content of the material, creates the appearance of accessing it for work purposes. The user seems to be sequentially reviewing and analyzing the information presented in the article.
Official Response of the CSM (Re-notification) - Update 13.09.2025:
Regrettably, the Superior Council of Magistracy has provided a hesitant response, failing to acknowledge its error and not taking the necessary measures to prevent such issues in the future.


CSM states that through rejust.ro, it is not possible to find out the case number (true), while omitting that the older platform, portal.just.ro, allows this procedure, which can lead to the de-anonymization of cases and enables the acquisition of access credentials to court case files.
First of all, although the statement that the national file number cannot be obtained is true, the CSM is aware of the existence of the platform and APIs provided by portal.just.ro, a platform developed by the Ministry of Justice with European funding.
Thus, by using the free public application portal.just.ro, a fingerprint can be created on the device + date + instance + case object to automatically identify the national number.
It is considered that CSM is likely aware of these risks, having participated in the implementation of the portal.just.ro platform. Nevertheless, they have determined that the risk of de-anonymization and subsequent unauthorized access does not constitute a significant enough risk to warrant a modification that might reduce the number of anonymized data.
The statement that CSM intervened quickly is true, but it overlooks the fact that both the initial and secondary interventions address the same technical issues, namely the inadequate anonymization of access passwords for the electronic files associated with the decisions visible on rejust.ro.
This means that, in fact, the interventions have been ineffective in addressing the issue, which has remained unresolved for an entire year. Even prior to this, the breach was accessible to the public since the platform's launch, for a much longer period.
In industry, such a response would be considered negligent, at the very least. Ultimately, the defense put forth by CSM claiming that terms and conditions or logging are necessary overlooks the simplicity with which cyber actors can evade criminal prosecution by using VPNs to conceal their true location.
The use of VPNs is widespread, implemented through obfuscation (making it difficult to identify the actual user of the VPN accessing the system at that moment) and, moreover, rarely logged. VPN providers market this feature as a benefit - absolute privacy.
Implicitly, any security measures based on punitive responses are ineffective - the prosecuting authority will be unable to take action to hold a non-state malicious actor accountable.
Regarding the national security risks arising from the large amounts of big data that may have been processed in the past, this vast quantity of information can be used to identify personal vulnerabilities of individuals of interest.
For example, a state actor could analyze the litigation history of a person of interest, identify that the targeted individual consumes pornographic content (information obtained from the electronic file in the victim's divorce) and/or has demonstrated proven infidelity, and decide to blackmail them with the publication of documents from the file to undermine their political capital. Another example is assessing the appetite for bribery by identifying behavior related to financially significant litigations.
An extreme but unlikely example would be analyzing information from medical certificates or medical documentation to uncover certain health issues of the individual that could be exploited.
All are becoming increasingly useful in the context where AI technology enables large-scale information analysis and the extraction of behavioral insights beneficial for sophisticated attackers.
Q&A: Cybersecurity Crisis in the Romanian Judicial System
Below are some answers to questions that I believe many would ask. I used AI to generate questions that logically arise from the information presented.
Q: How did you discover the vulnerabilities in the Romanian judicial system?
The first breach from the notification package sent to the CSM in August 2024 was this one, and I learned about it from a friend who is a tax consultant. The issue was so straightforward that he discovered it and mentioned it to me incidentally, without reporting it. I reported it to the CSM myself.
With 3 clicks, and using the phrase "use the password," the passwords for the files could be accessed through ReJust.ro. The vast majority of issues require a browser, a mouse, and a keyboard. No specialized software or technical knowledge is needed to exploit them.
Q: What is the actual extent of the breaches you have identified?
There are over 10 breaches that I have reported, none of which were voluntarily notified. The Official Gazette, the Cluj Court of Appeal, the High Court of Cassation and Justice, military courts, and over 80% of the courts in Romania have been exposed.
Millions of citizens have been exposed, with the highest degree of exposure occurring in the courts where documents in electronic files may include forensic certificates, details about domestic abuse, and other highly sensitive information.
Approximately 170,000 cases are within the jurisdictions of Constanța, Cluj, Târgu Mureș, Pitești, Craiova, Timișoara, any court that utilized the electronic case management platform of the Cluj Court of Appeal.
Q: What types of sensitive data are exposed by these vulnerabilities?
The category with the highest risk of systematic exploitation consists of family and minor-related cases. These include 4,904 cases of asset division and matrimonial regime liquidation, 837 cases of parental authority exercise, 688 cases of maintenance pension, and 129 protection orders.
In the field of economic crime, the 376 tax evasion cases and 698 insolvency petitions represent valuable sources for organized economic crime groups.
Sensitive criminal records, including 136 cases of domestic violence, 52 cases of pimping, and 20 cases of human trafficking, present a high risk of re-victimization.
Q: How did the authorities respond when you reported the issues?
The ANSPDCP has informed us that it is not the authority responsible for overseeing and sanctioning any potential data breaches by the judiciary, as this role belongs to the CSM.
CSM did not self-sanction, opting instead to conceal the issue and not apply GDPR regulations. The Judicial Inspection argued that there was no problematic act, nor any form of gross negligence that led to the publication of passwords in citations, which are public documents.
After nearly 12 months, I revisited the previously reported vulnerable websites to check if the issue had been resolved. I found that the resolution was superficial, still allowing access to files through the password.
Q: Is there evidence that these vulnerabilities are being actively exploited?
I know of several cases where, after notifying the authorities and making breaches public, economic operators who saw the subsequent disclosures informed me that they actively use similar breaches that the state has not yet detected, for economic purposes, curiosity, etc. Most of the breaches had been open for years and could have been exploited at any time by state actors.
The vulnerability appears to have been exploited in the wild, as brought to my attention by a legal professional who identified the issue while researching case law accessible through the rejust.ro platform.
Q: What happened after you publicly exposed the vulnerabilities of UNBR and CECCAR?
After I notified the victims, in the case of UNBR + CECCAR, they filed a criminal complaint which I believe will be dismissed. This is evidence that the system prefers to look for scapegoats rather than take action. I was summoned as a witness about a year later.
The prosecutor told me that what I am doing is good, but it puts me on the road. I have been subjected to attempts at intimidation through the actions of those responsible, which aim to discourage measures that would lead to their sanctioning. For example, the risk of having to go through the courts, needing funds for lawyers, etc., represents a form of coercion.
Q: What is the role of the company INTRACONNECT SRL in these breaches?
INTRACONNECT SRL is an example of an entity that was responsible for approximately 50% of the breaches in the information systems of public institutions. The same operator was also involved with UNBR, the eMAP system, and other platforms that I will not mention.
I don't know how contracts are awarded, whether there are security checks for them, or how their performance is monitored.
Q: What risks do these vulnerabilities pose to national security?
The system had several critical issues that allowed access to any account without a password. I also consider that admin accounts could be used to view all files, including archives of the program running on the information system.
In the long term, these issues could be exploited for destabilizing actions, for instance by falsely declaring a state of siege during periods when the authorities' response time would be longer. A decree could be issued establishing a state of war to generate instability among the population and incite an insurrection to overthrow the state order.
Q: Why isn't the CSM taking effective measures to resolve the issues?
The CSM exploits constitutional independence to evade the law and excessively invokes judicial independence to avoid imposing sanctions. The CSM controls the Judicial Inspection, which can remove judges from the system and leave them unemployed if they would fairly adjudicate cases involving their superiors.
The system is irreparably corrupt, and it seems that neither the government nor the political power can keep it under control, due to the enormous influence that the Constitutional Court has along with the Superior Council of Magistracy. Essentially, no law passes or is enforced unless they want it to.
Q: How does this situation affect foreign citizens and international relations?
Citizens from dozens of countries are involved, ranging from U.S. citizens to German, French, Italian, Emirati, and others. We have notified Germany due to its strict GDPR regulations and influence within the EU, and France because of our cultural ties and the support they provided us since our independence as a nation.
Romania has refused, for example, to assist me in ensuring my rights are respected on the grounds that I am a Romanian citizen and not a foreigner. Romania views its citizens as resources to be managed, while foreigners, due to the protection from embassies, have additional rights.
It is not the fault of foreigners, let's be clear, but ours for not respecting the rights of our fellow citizens, because they do not have any foreign embassy to guarantee them fairness in justice.
Q: What will happen if urgent measures are not taken?
We risk national security being exploited, not only by state actors but also by internal actors - con artists, scammers, hackers, etc. Likely, the breaches will be used by criminals, and the judicial system will collapse under the lack of public trust.
Judges risk losing all benefits if they do not prove they deserve them. It is unlikely that the system will be cleaned up without effort from civil society, regardless of political affiliation.
Q: What can citizens do to drive change?
My message is to address the authorities, even if they gain nothing from it. It is an effort that must be made for the country to recover.
Otherwise, at least they should seek assistance from the European Commission, as they would not appreciate being blackmailed with the fact that they were abused when they were younger, or possibly threatened that their children would be harmed if they did anything, because these vulnerabilities arise from documents inadvertently made public by the CSM or other authorities.
Ordinary citizens must hold parliamentarians accountable, file complaints with the Commission, and contact their countries' embassies for non-Romanians.
Q: Why do you continue this fight despite the reprisals and personal risks?
This is a moral and patriotic duty for a person who wants to have children in Romania. I do not believe that Romania can be saved in my generation, but I find satisfaction in trying to leave the country richer than I received it in turn.
Yes, I will continue to report vulnerabilities; I have even accepted the risk of potential reprisals, although I have taken measures to minimize these risks and to transform institutional abuses into other factors that can be monitored internationally.
Q: What is your conclusion about the current state of cybersecurity in Romania?
The reality is much worse than the perception. Unfortunately, public institutions do not adhere to even the fundamental rules of cybersecurity, conduct security audits only on paper, take no action, and there are reasonable suspicions that these behaviors occur in collusion with the assistance of public institutions and their interest groups.
The lack of transparency makes us prouder of the situation than the reality on the ground and leaves us vulnerable to unexpected attacks. Authorities and relevant institutions do not seem to be coping.
Q: Why do institutions not learn from repeated breaches and fail to take preventive measures?
Institutions do not learn from repeated breaches because the data of the litigants is deemed irrelevant, and the risks faced by ordinary citizens do not affect them.
Approximately 50% of issues are resolved only superficially, especially those requiring minimal effort from users - precisely the most dangerous ones because they are easy to exploit.
There are no penalties, only benefits - you don't put in initial effort, only on demand. When there are no penalties, a data breach is merely a task you postpone for the future, not a crisis.
Q: What is the actual capacity of control authorities such as DNSC and SRI, in your opinion?
The DNSC has limited capabilities in managing, similar to law enforcement institutions like the SRI. The judiciary wields significant power and seems to exempt itself from certain responsibilities due to the authority and real power it holds as the third branch of government.
The DNSC is very efficient, but the judiciary is strong and often resistant to "orders," so the DNSC's hands are somewhat tied, in my opinion. There are tens of thousands of tickets at the DNSC in the past year indicating that the issues are too frequent, yet it seems that the authorities refuse to comply with the DNSC's requests.
Clearly, what I am saying here is based on the effects I observe and the responsibilities I know the entities have, as no one provides me with a report. However, I believe it is quite clear when the game changes, and some responses indicate a coordination that requires training in such matters.
Q: What are the cases that receive quick attention versus those that are ignored for years?
High-stakes cases typically involve pressing political or national security interests, where the influence of law enforcement agencies surpasses that of the responsible authority, which is thus compelled to take necessary measures without evasion.
So far, UNBR, CECCAR, CSM, and the Official Monitor have been the main entities resistant to resolution due to a lack of interest; all are politically strong and influential. They have addressed many other issues, but only when there was institutional goodwill and at the institution managing the vulnerability.
Q: Why are victims not notified more than a year after the breaches were discovered?
The victims are not notified because GDPR is a concept largely ignored in Romania. The CSM has not yet informed the lawyers more than 11 months after the incident, and likely has no intention of notifying the victims for image reasons, even though the law requires it.
I would be glad if some professionals initiated lawsuits and sought damages; otherwise, these issues will never be taken seriously, and they will continue to be mocked.
Q: How does today's remedy demonstrate that the authorities were aware of the problem all along?
This morning, I re-notified the institutions and initiated the disclosure procedure regarding the existence of the vulnerability in a manner that does not pose a risk to the victims. Due to public pressure, the CSM resolved the issue in record time.
At 11:04 am, I confirmed the resolution of the issue, checking the platform multiple times to ensure there are no risks of sensitive data disclosure.
Now, the data is properly anonymized, with the password replaced by ***. This demonstrates that the CSM was aware of the vulnerability but maintained it until forced by public pressure.
Q: How do professionals utilize these vulnerabilities in their "toolkit"?
There are all sorts, primarily from IT platform providers that automate various aspects related to interactions with the state, to simple professionals who gather information using unintended advanced functions. There are dozens of people who understand the issues in Romania.
Professionals who include vulnerabilities in their toolkit, as they are often useful and rarely identified when actively exploited.
Economic operators engage in everything from industrial espionage to acquiring data that would otherwise be more costly.
Q: How is Romania monitored at the European level for these issues?
The EU is relatively limited in its ability to engage in domestic law but can request compliance with its regulations, especially when there are cross-border elements involved. Embassies also have an interest in protecting their citizens.
I have already sent memos to the European Commission because I want to poke them where issues cannot be resolved through backdoor deals.
Q: What is the true structure of power behind these issues?
The state is made up of interest groups, many of which are not concerned with the well-being of Romania as a country. Not because foreigners harm us, but because Romanians harm us and take advantage of the fact that we lack a guiding principle or authorities.
It is clear what risks there are to national security, considering how sensitive the data accessible through these files is and their high informational quality in many situations.
Q: What have you personally invested in this struggle, and what is the impact on you?
I have invested countless hours in identifying, reporting, notifying, and then going through the necessary procedures to resolve some of the more critical issues in this area.
The Romanian state pays for my plane tickets to testify due to the actions of corrupt individuals. Unfortunately, reporters like me are largely ineffective because, without pressure from other forces to hold accountable those responsible for the breaches, they are stuck with gum. However, I certainly cause maximum disruption.
Q: What are the most serious risks for victims whose data is exposed?
Trafficked women, victims of rape, abused children, individuals whose personal issues become public, companies whose financial troubles become a matter of public interest.
They would not like to be blackmailed with the fact that they were abused when they were younger, or threatened that their children would be harmed if they did something, as these vulnerabilities arise from documents inadvertently made public by the CSM or other authorities.
Organized crime groups may use this data to identify vulnerable victims or to protect their own operations by compromising witnesses.
Q: What do you expect from international pressure and embassies?
I expect Germany and France to exert pressure, even if quietly, on the Romanian state. I will notify several embassies to hold them accountable as well, and to increase the likelihood that they too are compelled to take measures in favor of their own citizens to avoid criticism in their own country.
I will notify the embassies in the order I am responsible for doing so to reduce the risk of them exploiting vulnerabilities or information regarding the weaknesses of the current system. All embassies notified so far are in NATO, with most being from the EU.
Relevant documents (original)
This list will also be completed with the reports submitted to public authorities, once the resolution of all issues is confirmed, so that I do not post strictly redacted information that could further jeopardize the victims' data more than it already has.
Invitation to anyone who wants additional evidence regarding the breach to submit requests under Law 544/2001, or to contact me via email at office@incorpo.ro, where I will be limited in the amount of information I can disclose.
Furthermore, I have already submitted the information to the relevant parliamentary committees, and I hope they will uphold the rights of citizens.
Consider that it is the role of lawyers to protect the parties they represent and their private lives.
I will communicate with the European authorities to ensure that the judiciary is held to the same standard of accountability as the other branches of government.
Old resources - Public Discussions:
CSM vulnerability that exposed access data for over 150,000 files
by u/incorporate in legal
