What should I do if I have been a victim of a data breach?

If you have suffered a data breach, been a victim of a ransomware attack, or something similar, you may find yourself in a position where you have both lost data and a malicious actor threatening to disclose that data unless you pay a certain amount of money, along with clients who may want to express their anger towards you.
In this article, I aim to explain how to manage such a situation at a macro level, from the perspective of a manager or company administrator.
Why do data breaches occur?
More and more activities are now being conducted online. Technology is very useful to us and has become indispensable in both our personal and professional lives, with its pros and cons.
A negative effect of widespread technology adoption is that intrusion is no longer limited to the physical realm (someone breaks your shop window, enters through the window, and steals), but extends into the digital sphere as well.
Unlike a thief, who leaves traces when "stealing" in the physical environment - their appearance can be seen on surveillance cameras, making them traceable and often identifiable, a hacker is much more difficult to identify and manage.
Nowadays, it is easy to commit cybercrimes. From simply accessing a partner's password-protected phone out of jealousy to engaging in high-risk criminal activities such as launching cyberattacks, the internet provides everything you need to cause significant harm to individuals and businesses alike.
The vast majority of vulnerabilities exploited by hackers are published by security researchers who identify theoretical issues and make them public. Malicious actors monitor these well-intentioned reports, identify what has been resolved in the updated version, and exploit the adoption gap of new versions to utilize public vulnerabilities and gain access to the victim's computer.
Some of the vulnerabilities also include 0-day exploits, which are obtained by more capable malicious actors who often employ much more advanced methods to attack a victim. However, these actors are few and typically target larger entities than a corner store or a business with a turnover of under 500,000 RON.
How can I ensure that I am not a victim of a data breach?
In short, you need to allocate resources in this direction. Money and/or time - either an employee or yourself to handle the technical side, ensuring you have the necessary software, etc.
Within the budget, you can cut costs. Microsoft's antivirus is good on its own. If you keep your computer updated with the latest versions and don’t mind Windows updates, it’s not advisable to use cracked software, as it limits your ability to update and exposes you to significant risks. There are affordable keys available online that work.
It is advisable, if possible, to allocate a technical person to handle these tasks, especially if you have a relatively large team (5+ people). This can be part-time or contractual (the latter is preferable in terms of costs).
Create backups in case of force majeure and make sure you have someone to contact (lawyer) in case of force majeure, to help reduce your subsequent costs.
What should I do if I am a victim of a data breach?
In short, it's complicated - either you pay the fee and have a 60%-40% chance of getting your data back, or you recover from backups (if you have any), or you go into damage control if you don't. That's why it's important to have backups.
Step one, assess the situation and halt the attack.
The first step is to unplug everything. I may be exaggerating in the case of large entities where SLAs matter, but I speak very seriously for small businesses. If you are not a technical entity and do not know how to manage such projects, it is better to shut down all technology (including cutting off the power) than to risk someone tampering with your computer while you try and fail to catch them with antivirus software.
A large company usually knows how to troubleshoot what might happen and to analyze external factors (such as the heat emitted by servers/workstations) to determine if the workstations are problematic to keep running.
By shutting down the calculator, you lose some forensic artifacts, but you increase the chance that a measure like encryption or a delete all will fail, compared to leaving them running where a 'rm -rf /*' command could hit its target and delete data that could otherwise have been preserved.
Sometimes keeping them powered on allows you to recover keys from RAM or other techniques that can retrieve your data, but for that, you need a technical person on-site (most don't have one) to shut down the live encryption process and immediately call in experts with hourly intervention fees in the five-figure range, so large companies do not shut down servers/computers but strictly the network.
If you are on this article, it’s clear that you don’t fit in there and you already know what to do - so there’s no point in providing you with explanations that are already well-known in the industry for technical people.
Antivirus software does not detect everything, especially zero-day vulnerabilities, and if you act recklessly, you may worsen the situation significantly. Normally, anything that is affected or at risk should be removed from the network, air-gapped (disconnected from the internet), and cleaned manually, possibly restored from a backup if the attack appears to be executed by an actor capable of leaving backdoors.
However, you need to identify when and how it entered your system, because otherwise you risk serious consequences. You restored from a backup, it re-entered (possibly from an infected backup), and it could take your data again in another year, this time demanding a larger ransom.
First, we need to address these issues, but we will return to step 3 where we will discuss how to do this. For now, we need to minimize the attack surface and know what to say to clients/authorities as needed.
Step two, notifying public institutions and clients
In theory (and I encourage you to comply with the law), at the second instance a criminal complaint should be filed with DIICOT, along with a "self-report" - a notification to the press at ANSPDCP. The latter will impose a hefty fine (5-10k EUR), but that is the correct course of action.
The reporting obligation to ANSPDCP does not exist if the data breaches do not affect any individual; however, the vast majority carry such a level of risk.
However, most companies do not report events to the ANSPDCP to avoid fines; at least according to ANSPDCP reports, these situations seem to be very few, which indicates to me a selection bias. Romanians tend to hide their faults, and I know that in my own reported vulnerabilities, the ANSPDCP was not notified. I have reported dozens to public and private institutions, all with a high level of risk. I am not aware of any entity being sanctioned.
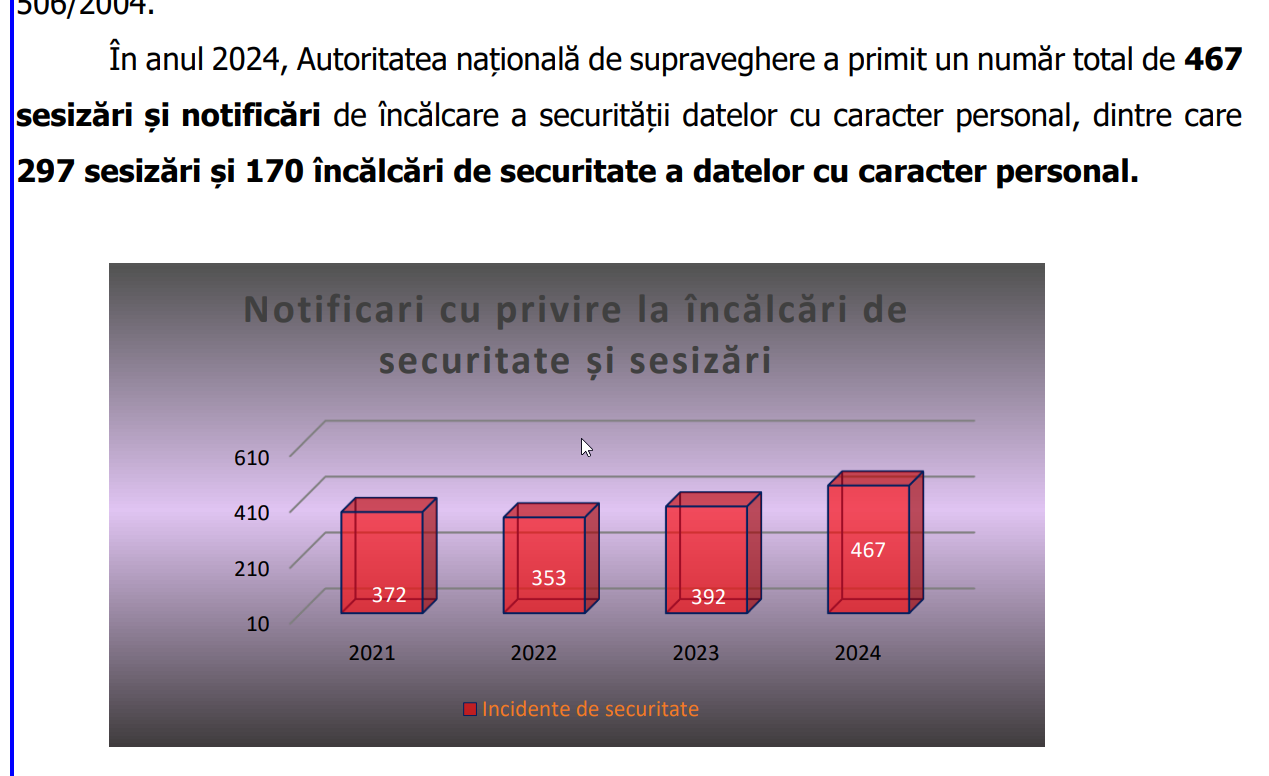

The official reports regarding the activity of ANSPDCP, where the relatively poor state of Romanian self-reporting can be observed.
It's your decision whether to proceed, but generally, if the hacker doesn't put the data online (which is quite possible if the data is appealing, but unlikely if the data is mundane and not easily used for blackmail), you are safe and unpunished.
If they put it online, it depends on whether the ANSPDCP self-notifies (low to medium chances). If the ANSPDCP self-notifies and you haven't reported it, you're in serious trouble unless you have a good lawyer, and you can delay/refuse to cooperate honestly/justify yourself by exploiting the limits of the ANSPDCP's competence and authority (meaning you claim the data is false, that it’s not from you, etc.).
Many have practiced this before, including public authorities, seemingly with success, but it is risky and constitutes a criminal act, so I do not encourage it. This is not how problems should be solved in any case, and such conduct affects your reputation in the long run. However, I will not be ignorant of the institutional vulnerabilities we have as a country, and it is up to the entrepreneur to decide what actions to take.
Legally, you have an obligation to notify, and fines can reach percentages of your turnover, so the larger you grow, the more advisable it is not to neglect reporting. A fine is manageable if you do not inflate it yourself with unjustified risks.
Then, you must notify the clients, providing a brief summary of the measures the company will take to prevent such incidents in the future, as well as the risks they are exposed to and how to mitigate them. If you are acting in good faith here, it is bad but not very bad. I have seen vague messages being used, based on the principle of minimal compliance with legal obligations.
If this works, because in theory a vague 2-line email exempts you from clear legal liability for violating GDPR. In theory, you shouldn't, but in practice, it's possible for the court to forgive you and you might escape with a smaller or no fine. I've seen this in practice because it creates an appearance of legality without generating the anxiety associated with a responsible message. Immoral, but it is practiced.
Please hire a lawyer as fines can be substantial, and they can help reduce them, especially if you decide to comply with the legal obligation. I won't lie by saying that the legal obligation for self-reporting is often adhered to, but if you are sensible and report, still get a lawyer to help mitigate your future fine costs.
Step three, mitigate the attack
After you have addressed your legal obligations, mitigate the attack and see what you can do (restore from backup, recover the current system).
Some ransomware attacks use vulnerable malware that can be deactivated later. Other ransomware attacks are foolproof, and you either have the option to pay the person (on trust) with a 60% chance of getting the decryption key back, but your data remains on their computer (and it's possible they may ransom it again in the future). Or they might just scam you.
It is difficult to estimate how many malicious actors are trustworthy - after all, I wouldn't say that criminals are the most reliable people, but probably most of them will give you the encryption key after they have done their job for the following reasons:
- Not all clients are valuable enough to justify stealing their data and making it public, as they possess information that cannot be monetized otherwise.
- Typically, the price of exfiltrated data is an order of magnitude lower than the payment for ransomware, especially if the malicious actor has a reputation (which is necessary for people to trust that they will keep their word and return the money). It's risky to scam because you may gain in the short term but suffer in the long run. Plus, it doesn't cost you anything to give them the decryption key after you take it from them.
In any case, this shouldn't be the first option - if the data exists in a backup or hasn't been encrypted, it's best to restore from there and not give anything to the malicious actor.
If you truly have mission-critical data, where the decision to act morally could cost you your entire business, I leave it to you to decide. The morality is debatable if by not paying the ransomware your clients lose more money than the extortion would cost you.
I will explain how you can pay a protection fee in the last part of the article, although I discourage such behaviors. You decide if it is worth the price, and sometimes it may be possible to do so.
Step four, prevent an attack from happening in the future
It's pointless to mitigate one attack if another is coming soon. In my opinion, you must do everything possible to prevent a future attack.
How do you do this? Simple, you create a backup with redundancy (using the 3-2-1 method),
- 3 copies of the provided data, one being the one you are working on (production + staging), and the other two as backups.
- 2 different storage solutions. For example, you can have a local backup and one in the cloud. Affordable options include Hetzner Storage and Backblaze, but there are hundreds of solutions available, each with its pros and cons.
- Data must be stored off-site, meaning not at the business location. In case of a fire at the headquarters or a nuclear bomb, the data should survive. undeva. Usually in the cloud.
Then, make sure you have an up-to-date antivirus, perform regular backups for both applications and the operating system itself, and ensure you separate concerns within applications, meaning you should have some rules for information hygiene.
Be careful not to use the same passwords in multiple places (or at least have different levels of passwords based on the inherent risk of each application you access, keeping in mind that some will be compromised and your password will be public sooner or later).
Therefore, it's essential to have a disaster plan in place to effectively manage future crises when they arise. Typically, companies, especially small ones, do not consider this, even at an abstract level, and are overwhelmed by an attack, not knowing what to do.
The situation is complicated, and it would be absurd to say that there is a solution that takes into account the inherent difficulties in managing a small business.
Finally, educate your employees. They are often the most dangerous link. They click on emails they shouldn't, are gullible, and use weak passwords that they also use at work.
I personally experienced two data breaches involving emails, both due to collaborators mishandling their computers where they stored their work passwords. Fortunately, we separate concerns, so nothing sensitive was accessed. They only sent spam from my emails, and this was limited after the first incident where my mail server was used for spam, prompting me to implement rules to restrict high throughput (to prevent sending too many emails).
Step five, face the consequences
The reality is that there will be consequences for being negligent / not allocating enough funds for incident prevention.
The extent of the costs will depend on the severity of the attacker, the size of your target, and the type of data you have lost (we're talking about medical data, legal information, or a breach of accounts used strictly on your application).
If you are clever, the lost data won't be very important, and the costs for you will be low. However, if you overlooked these aspects, the costs could be significant.
If you have reported institutionally that you have suffered a breach, you risk facing serious consequences, or if luck is on your side and the attacker was negligent, you may be able to obtain compensation from them (assuming they have the means to pay, and that those funds can be seized, especially if they are in a crypto wallet where, if the malicious actor is savvy, they might hold onto the money).
Bonus: How to pay the extortion
If you find yourself in the unfortunate situation of having no better option than to submit to extortion and pay a protection fee, below we will teach you how to do this quickly and (relatively) safely.
Establish a means of communication with the attacker
Establish a means of collaboration with the malicious actor in a way that helps you better understand the likelihood of them keeping their promises. Typically, they will attempt to use untraceable means of communication (e.g., Signal, anonymous emails, etc.).
If they are traceable, report to the prosecuting authorities. If you manage to give them an IP logger (send them a file to download from your system, a link where you can log their activity, etc.), report to the prosecuting authorities. If they are smart, keep this in mind as it reduces your chances of negotiating.
If you decide to pay the "redemption," a prior discussion is mandatory. Here you can discuss what mechanisms you implement to avoid any party being at a disadvantage, and possibly negotiate the price further.
If the malicious actor does not identify themselves with a digital persona (such as a hacking group, a username in a hacker group, etc.) in a traceable manner (for example, by leaving a message from their account), the risks are that you could be scammed.
If they tarnish the reputation they have worked hard to build, the cost of blackmail may not be enough to cover their reputational losses. This is an advantage for you if you decide to return the money. But make sure they have more to lose than what they are demanding from you in blackmail.
Typically, these actors are sociopaths but rational, so you can negotiate with them if you present clear arguments. For example, if he shows you that he is someone, but does not have a well-established reputation, you can lower the price by reaching a consensus on the principle that he cannot guarantee he will keep his promise. Be cold with him, show no emotion, and usually, you can cut the price.
The rule applies mutatis mutandis to all immoral individuals you collaborate with or interact with. If they have ego issues, exploit them. Most are also narcissists or have other personality problems that can be leveraged to cut your costs.
Find a way to notify the malicious actor that you will seek revenge if they do not keep their promise—damaging the reputation they previously established, but consider how to do this without further harming your own reputation.
The idea of having paid blackmail to an individual is not very favorable, and if you don't show the actor that you have some leverage over them in case they try to deceive you, they might completely take advantage of you.
Buy cryptocurrencies to pay the protection fee
You use a CEX to buy cryptocurrencies with cash. I'm not sure if such amounts are deductible or what their tax implications are. However, I assume they are expenses clearly in the interest of the company. I don't think ANAF will report further to ANSPDCP because it would be a significant effort, but they can disallow the expense even if there might be an economic and purely fiscal justification for it.
Good examples of CEXs that have not proven to be Ponzi schemes so far include Binance, Coinbase Pro, and Kraken.
Ideally, if you can, notify the CEX about your intention to pay a ransom, as they may block the respective accounts (if they are on exchanges) or impose limits on accounts to make it more difficult for the malicious actor to launder the money. This must be done in advance. A qualified lawyer in this niche can assist you, and there are few available.
You pay the offender
You can find the crypto address of the malicious actor. If you are collaborating with public institutions, it is advisable to discuss a potential ransom with them so that they can coordinate it, as the malicious actor may expose themselves by laundering the money (or failing to do so). Sometimes you can link the paid money to the guilty party and recover part of the funds this way. The chances are slim as the malicious actor becomes more sophisticated.
It is likely that he wants either Bitcoin (which has high liquidity and is integrated into money laundering platforms) or he may prefer Monero or other cryptocurrencies that are harder to trace. He will probably want Bitcoin.
Buy Bitcoin from these platforms.
After you make the payment, all you can do is hope that the person who committed the prior offenses will keep their promise and adhere to this arbitrary rule of refunding your money. Typically, the malicious actor is incentivized to honor their promise, especially if they have a persona that claims the attacks.
The result of your actions
If he doesn't keep his promise, embarrass him in a way that is accessible as I previously described. If there isn't a mutually understood way to hold him accountable for a potential scam, he has every incentive to do so and sell your data afterwards.
If he keeps his promise, use the encryption key to decrypt the data and verify its integrity. It is very likely that there is still a backdoor. Scrutinize the data and check for and eliminate any leftover junk.
If you are careless here, you might have to pay the protection fee again. Criminals are looking for easy targets, so don't be an easy target.
Conclusion
Offenders in these areas are well-prepared while public institutions lag behind. The nature of the internet resembles the Wild West - it is very difficult to obtain justice in an environment lacking traceability, where fault is hard or even impossible to assign.
In today's digital world, the costs of investigating these attacks exceed a million dollars, so the chances of authorities taking the case seriously if it proves difficult are minimal.
Don't rely on DIICOT or any IT specialist you might know to save you. Take precautions in advance to avoid becoming a victim, as the consequences in the alternative scenario are much greater.

